Protecting Your Organization from Token Theft: Bypassing Multi-Factor Authentication
Token theft is a growing concern for organizations that rely on multi-factor authentication (MFA) to secure their systems and data. In this article, we will explore what token theft is, how it occurs, and what steps organizations can take to prevent it.
Understanding Token Theft:
A security vulnerability in Microsoft 365 allows hackers to steal authentication tokens and access user accounts. The issue is caused by a weakness in the way Microsoft handles authentication tokens, allowing hackers to reuse them on different devices. The attack is typically targeted and requires some knowledge of the victim’s email address and other basic details.
Once a cybercriminal steals an authentication token, they can use it to access company resources without needing the user’s credentials or MFA. This is because the token contains a trusted user identity recognized by the domain the user interacts with.
How Token Theft Works:
Attackers have several methods for stealing authentication tokens, with two of the most common being phishing and malware attacks:
- Phishing Attacks: An attacker sends a phishing email or message containing a link that appears legitimate. When the victim clicks on the link, they are prompted to sign in to their Microsoft account. The attacker then captures the authentication token from this process and uses it to access the victim’s account without needing further credentials or multi-factor authentication (MFA).
- Malware Attacks: In this scenario, the attacker sends a phishing email or message with a link to a malicious site designed to inject malware into the victim’s system. Once the malware is installed, it captures authentication tokens and relays them back to the attacker. The attacker then uses these tokens to access user accounts, bypassing the need for passwords or MFA.
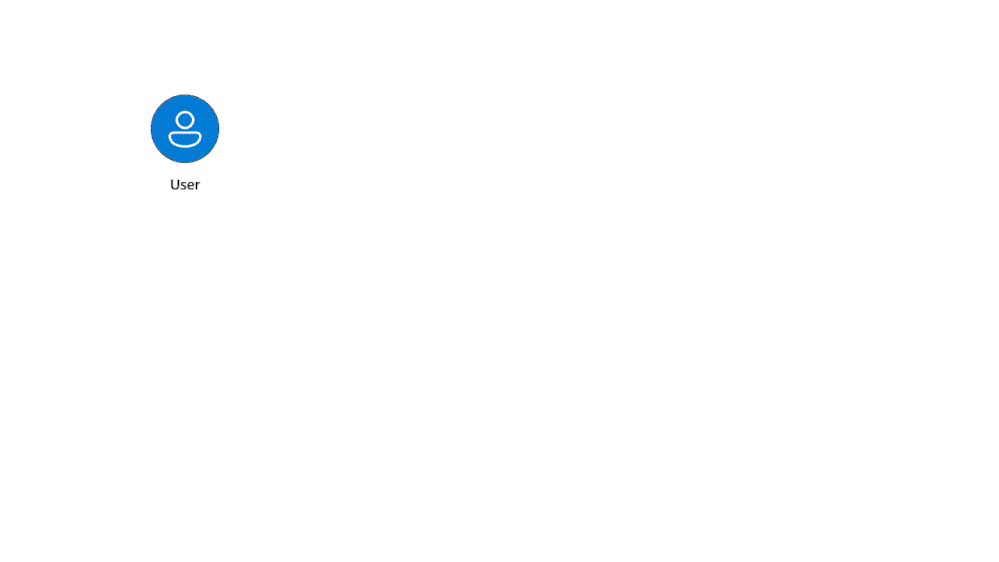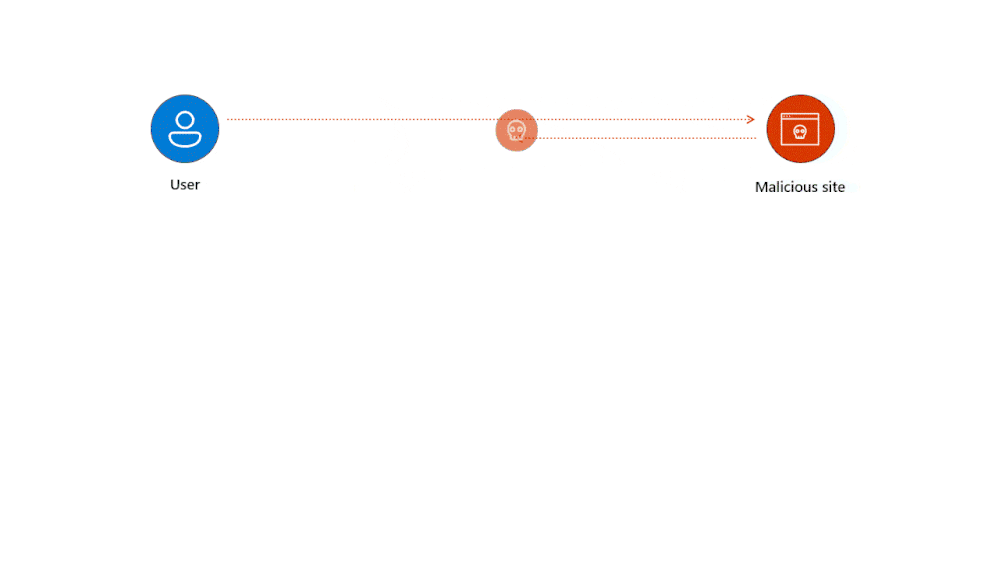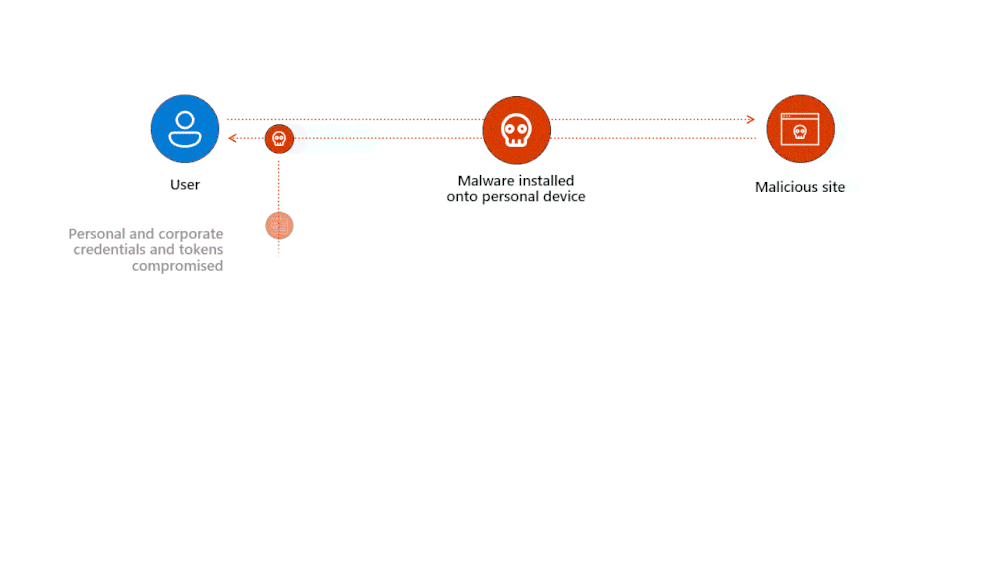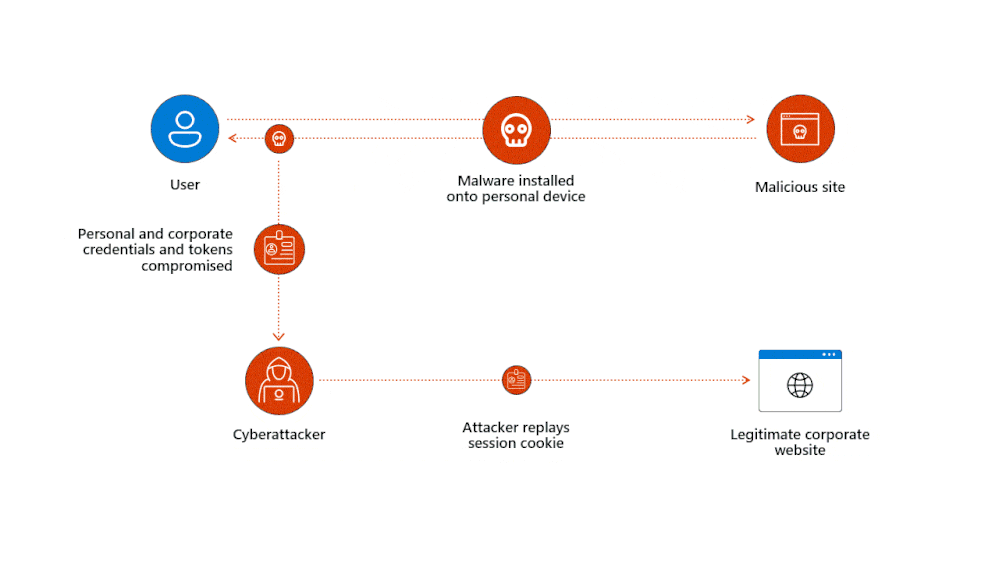
Preventing Token Theft:
To prevent token theft, organizations can take several steps, including:
- Ensuring that every device accessing company resources is a known device visible to the IT team.
- Implementing MFA solutions that are phishing-resistant.
- Educating employees about the risks of phishing attacks and how to spot them.
- Use conditional access policies to restrict sign-ins to specific countries or locations.
- Implement a robust identity protection policy to detect and block suspicious sign-in activity.
- Implementing strong password policies and regularly monitoring user accounts for suspicious activity.
- Leverage an XDR solution to automatically respond to detected threats by isolating compromised devices and accounts.
- Configure identity protection to evaluate sign-in locations and detect impossible travel scenarios.
Token theft is a growing concern for organizations that rely on MFA to secure their systems and data. By understanding how token theft occurs and taking steps to prevent it, organizations can protect their systems and data from cybercriminals. Ensuring known devices, implementing phishing-resistant MFA solutions, educating employees, robust identity protection policy to detect and block suspicious sign-in activities, and monitoring user accounts are all critical steps in preventing token theft.
Don’t let your organization fall victim to token theft. Take proactive steps today to secure your systems and data. Contact Britec for a comprehensive security assessment and to learn more about implementing advanced MFA solutions and identity protection policies. Protect your organization from cyber threats now!

